Published on
Keeping your software secure is not a set-it-and-forget-it process. Regularly monitoring and keeping up to date on patches are vital to maintaining a system that cannot be attacked. Understanding the types of data you should not share with AI is also crucial for reducing exposure to risks caused by insecure integrations or careless data handling.
This article will review what Software and Integrity Failures are and provide recommendations for protecting against them.
Read More About OWASP Top 10: OWASP Top 10 Security Logging and Monitoring Failures Explained
What are Software and Integrity Failures?
Software and data integrity failures are vulnerabilities in software or infrastructure that allow an attacker to modify or delete data in an unauthorized manner. Attackers can exploit these vulnerabilities to gain access to sensitive information or cause damage to the system.
Some examples of software and data integrity failures include:
- Insufficient Verification of Data Authenticity: This occurs when the software does not properly verify the data source before it is processed. This can allow an attacker to inject malicious data into the system.
- Missing Support for Integrity Checks: This occurs when the software cannot verify data integrity. This can make it easier for an attacker to modify or delete data without being detected.
- Untrusted Search Path: This occurs when the software allows an attacker to control the search path for libraries or modules. This can allow an attacker to inject malicious code into the system.
- Download of Code Without Integrity Check: This occurs when the software downloads code without first verifying its integrity. This can allow an attacker to inject malicious code into the system.
- Deserialization of Untrusted Data: This occurs when the software deserializes data that has not been adequately verified. This can allow an attacker to inject malicious code into the system.
Real-Life Example of Software and Integrity Failures: WannaCry
In 2017, a ransomware attack called WannaCry infected over 230,000 computers in over 150 countries. The attack used a vulnerability in the Windows operating system to spread. Once infected, the ransomware encrypted the victim's files and demanded a ransom payment to decrypt them.
The WannaCry attack caused significant damage, with estimates of the total cost ranging from $80 million to $1 billion.
Read More on CSO Online: WannaCry Explained: A Perfect Ransomware Storm
How Can You Protect Against Software and Integrity Failures?
The key to preventing software and integrity failures is to monitor third-party software and ensure the implementation of all security updates and patches promptly to ensure the software's and data's reliability throughout the software development life cycle.
Compile a Software Bill of Materials (SBOM); this allows for a better understanding of the application's structure and makes it easier to identify which components need updating.
Regularly monitor for updates and security patches for all components and apply these updates swiftly to help minimize potential risks associated with vulnerabilities.
Replace components that are no longer supported or have known security vulnerabilities to ensure that the application only uses up-to-date and secure components.
Use a Software Composition Analysis (SCA) tool to detect and report any vulnerable components in the application, thereby automating the process. This enables your team to address the identified issues and reduce potential risks quickly.
Establish a reliable and repeatable process for updating and patching components to ensure the application remains resilient and in line with the latest security standards.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to enhance security awareness and build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to engage/grow a security champions program -- whatever works best for your organization.
In Chapter Nine, The Diligent Developers are Conquering the Shape-Shifting Serpent of Software and Integrity Failures:
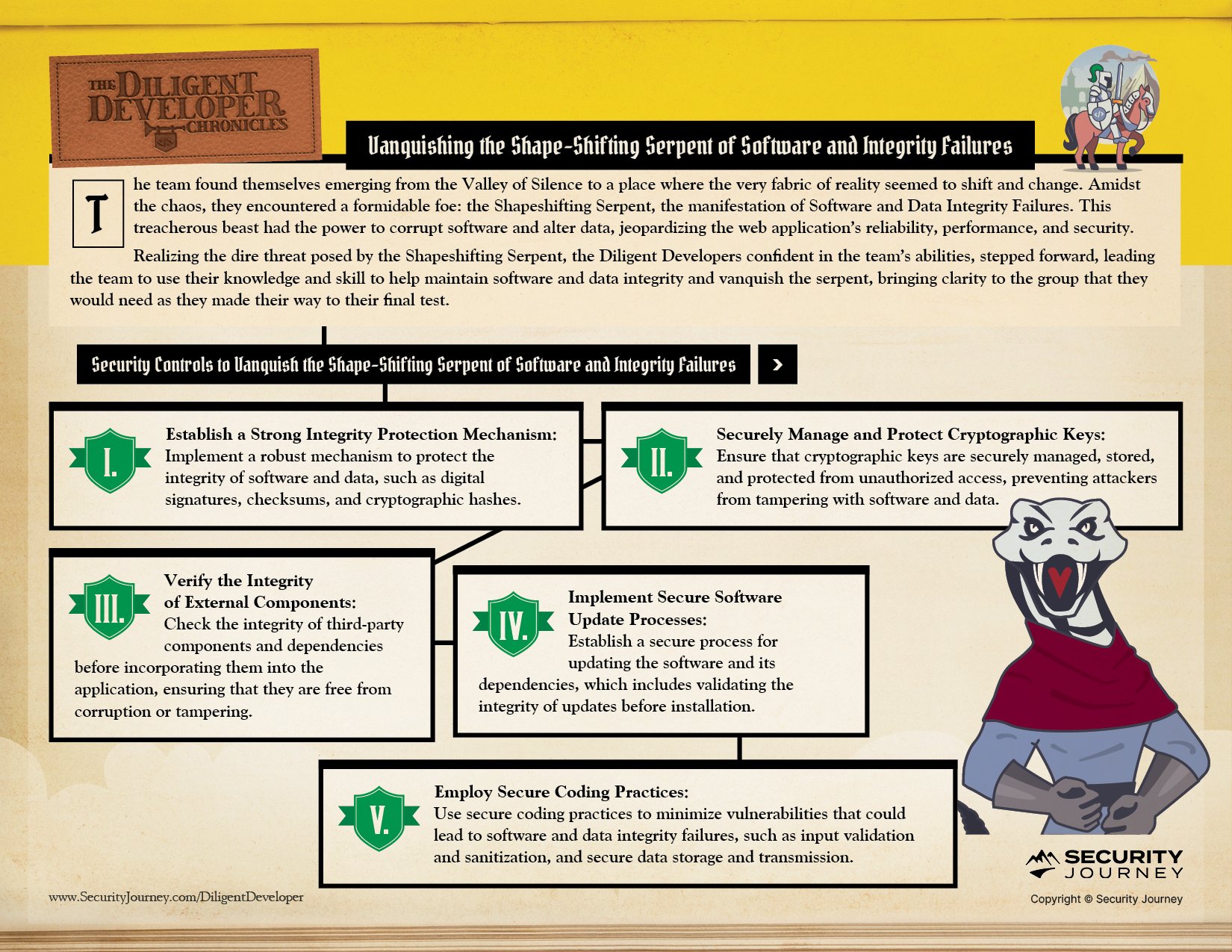
As The Diligent Developers continue their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to effectively train your organization on OWASP Top 10 vulnerabilities.


