Published on
So, you set up your security framework and monitor events regularly, but do you log security vulnerabilities and actions you took to stay secure?
In this article, we will review what Security Logging and Monitoring Failures are and provide recommendations for protecting against them.
Read More About OWASP Top 10: OWASP Top 10 Identification and Authentication Failures
What are Security Logging and Monitoring Failures?
Security logging and monitoring failures are security vulnerabilities that can occur when a system or application fails to log or monitor security events properly. This can allow attackers to gain unauthorized access to systems and data without detection.
Some of the most common security logging and monitoring failures include:
- Not Logging Important Security Events: This can include failed login attempts, unauthorized access to sensitive data, or changes to system configurations.
- Not Monitoring Logs for Suspicious Activity: This can include repeated failed login attempts, unusual traffic patterns, or changes to system configurations.
- Not Storing Logs for Long Enough: This can make it challenging to investigate security incidents that occurred in the past.
- Not Having a Process for Reviewing and Responding to Security Logs: This can allow security incidents to go undetected and unaddressed.
- Insecure Logging and Monitoring Systems: This can allow attackers to access or modify logs, making tracking their activities difficult.
Real-Life Example of Security Logging and Monitoring Failures: 2013 Target Data Breach
Attackers gained access to Target's network through a vendor portal that third-party vendors used to access Target's systems. Once they had access to the network, the attackers were able to install malware on Target's point-of-sale (POS) systems to steal the credit and debit card numbers of customers.
One key contributing factor to the breach was that Target did not properly log failed login attempts, which allowed the attackers to try different usernames and passwords until they were successful. The stores also did not monitor their logs for suspicious activity, such as repeated failed login attempts from the same IP address.
Read More on Slate: We Still Haven’t Learned the Major Lesson of the 2013 Target Hack
How Can You Protect Against Security Logging and Monitoring Failures?
The key to protecting against security logging and monitoring failures is to log all critical security events and monitor them for suspicious activity. Let’s dive into what that means:
Ensure comprehensive logs are generated, capturing essential security events, including user authentication, access control, and data manipulation. This allows for effective tracking and detection of any malicious activities.
Securely store and protect log files to ensure their integrity and confidentiality, including measures to prevent tampering and unauthorized access, preserving the reliability of the logged data.
Implement a process to regularly review and analyze logs with both automated tools and manual inspection to detect possible security incidents and emerging threats.
Set up real-time monitoring and alerting systems to detect and respond to security events swiftly to lessen the impact of attacks and prevent potential breaches.
Create a comprehensive incident response plan that clearly outlines roles, responsibilities, and procedures to be followed to ensure a prompt and coordinated response to security events detected.
Commit to a path of continuous improvement by drawing insights from past incidents and evolving threats, to enhance logging and monitoring practices, adapting to emerging challenges, and fostering a proactive security stance.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to enhance security awareness and build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to engage/grow a security champions program -- whatever works best for your organization.
In Chapter Eight, The Diligent Developers are Taming the Whispering Shadow of Security Logging and Monitoring Failures:
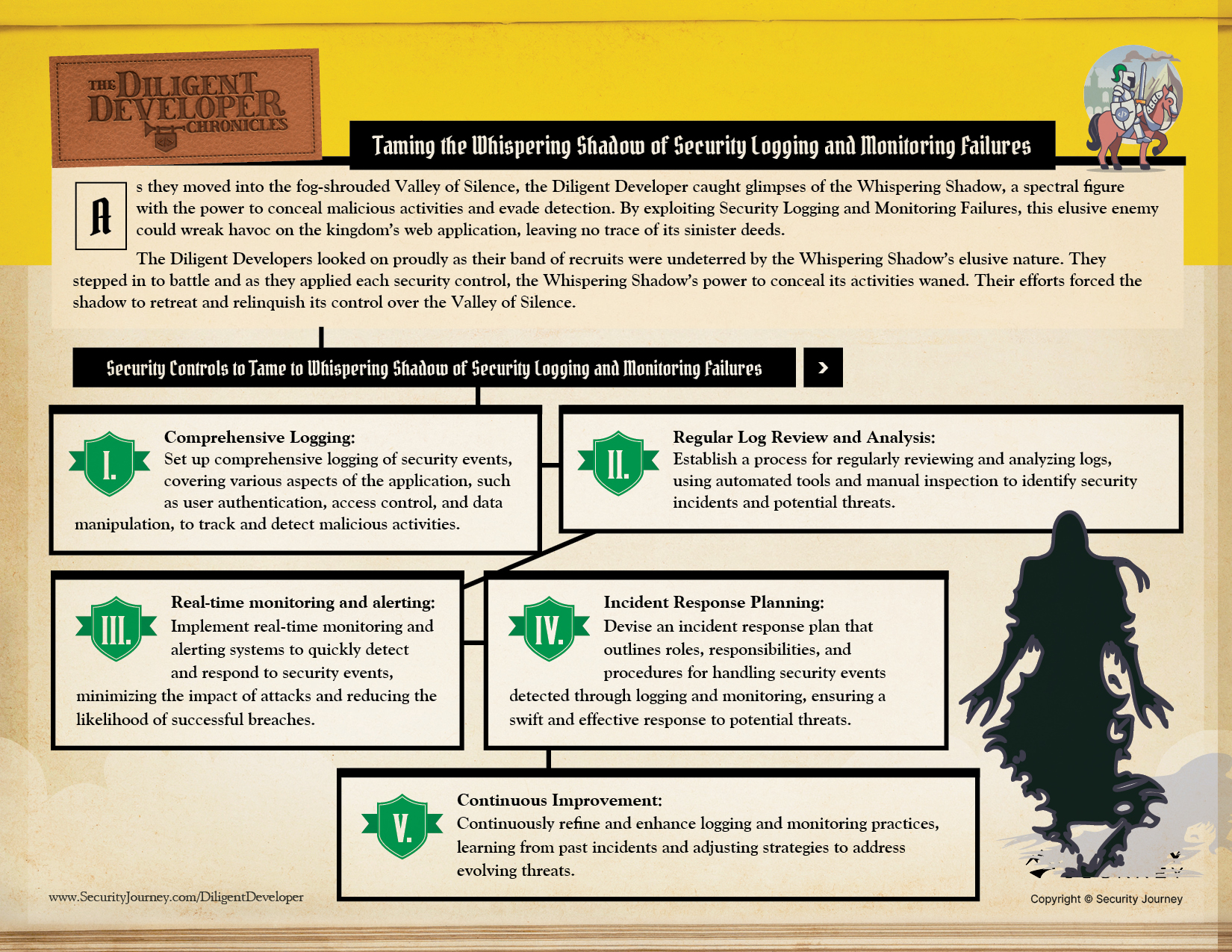
As The Diligent Developers continue on their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to train your organization on OWASP Top 10 vulnerabilities effectively.


