Published on
The OWASP Top 10 is a crucial guide for the AppSec community, highlighting the most common vulnerabilities developers should keep in mind.
In this article, we will concentrate on Insecure Design and provide recommendations on how to avoid it in your code. We also suggest The Diligent Developer Chronicles as a great training tool for your development team.
Read More About OWASP Top 10: OWASP Top 10 Injection Attacks Explained
What is Insecure Design?
Insecure design is a software design flaw that can make an application vulnerable to attack.
It is a broad category that encompasses a wide range of weaknesses, such as:
- Lack of Input Validation - The application does not properly validate user input, which can allow an attacker to inject malicious code into the application.
- Improper Session Management - The application does not properly manage user sessions, allowing an attacker to hijack a session and take control of the victim's account.
- Insecure Data Storage - This means that the application does not properly store sensitive data, allowing an attacker to access and steal the data.
- Insecure Communication - The application does not properly secure communication between the client and the server, allowing an attacker to intercept and modify data.
Read More: OWASP: A04:2021 – Insecure Design
Real-Life Example of Insure Design: Equifax Exploit
In 2019, a vulnerability in the design of the Equifax credit reporting agency's website allowed attackers to steal the personal information of over 147 million people. The vulnerability allowed attackers to inject malicious code into the website's search bar, which allowed them to access sensitive data from the website's database.
The exploit was discovered by security researchers at Check Point Software Technologies. The researchers reported the vulnerability to Equifax, but the company did not fix the vulnerability until several months later.
Equifax was fined $700 million for the breach. The company also implemented several security measures to prevent future breaches.
Read More on CNN: Equifax Exposed 150 Million Americans' Personal Data
How Can You Protect Against Insecure Design
The key to protecting against insecure design is considering security from the start and throughout development.
This means that security should be a top priority for everyone involved in the development of a system or application, from the initial design phase to the final deployment. By considering security from the start, organizations can help to prevent security vulnerabilities from being introduced into their systems and applications.
Here are some ways you can prevent Insecure Design within your code:
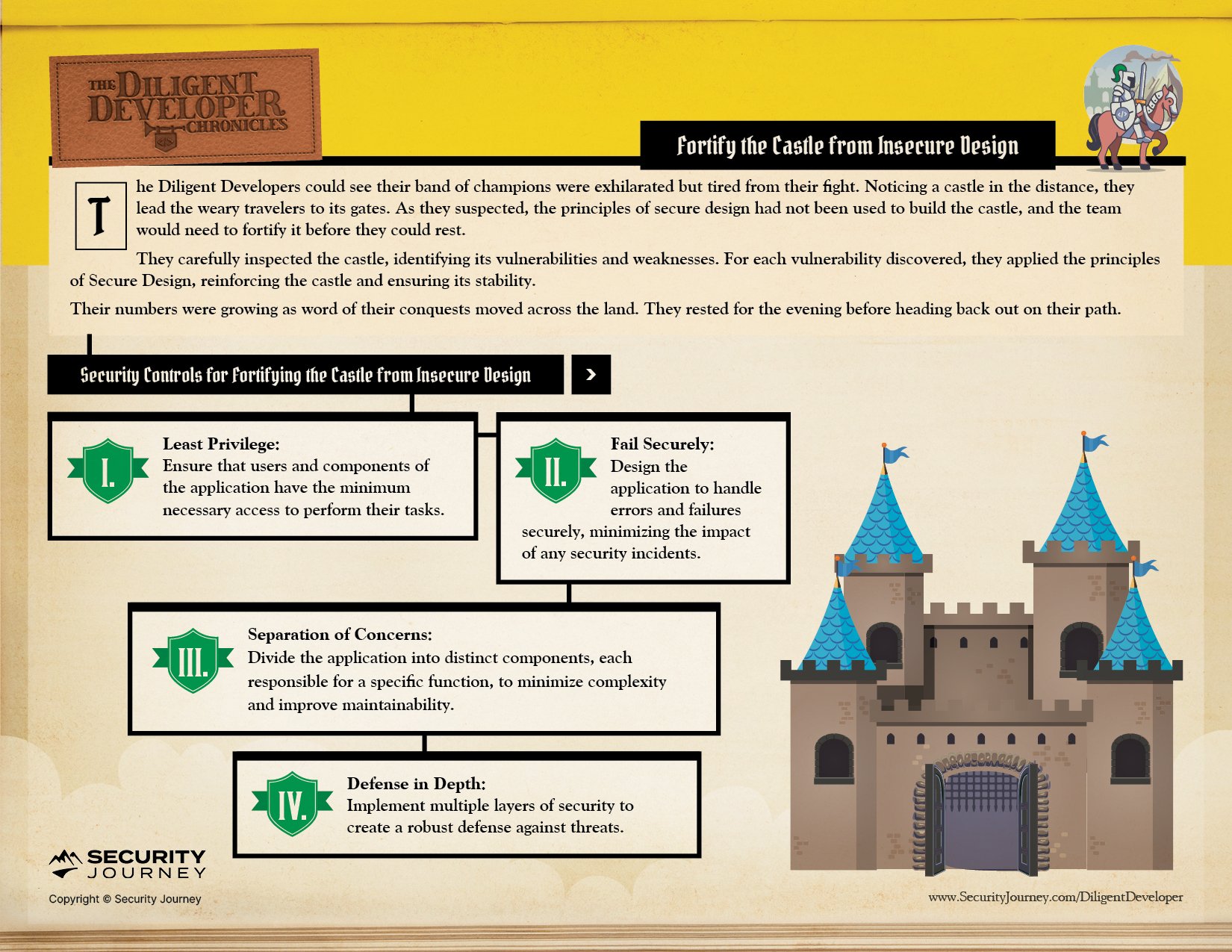
Principle Of Least Privilege ensures that users and components of the application only have access to the bare minimum necessary for their tasks.
Principle of Defense in Depth establishes multiple layers of security, creating a robust and intricate defense mechanism against any potential threats.
Fail Securely Principle means designing the application to handle such incidents securely, to minimize the consequences of security breaches or accidents.
Secure by Default means that systems and applications should be configured in a secure state by Default. This means that security should be built into the system from the ground up and should not be an afterthought.
Principle Of Separation of Concerns means dividing data into distinct components, each assigned a specific function. This pragmatic approach reduced complexity and facilitated easier maintenance, ultimately enhancing the app's overall security.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to stay aware of prominent vulnerabilities and code risks, but also engage in continuous training and conversations about code security across the organization—an approach that strongly aligns with the principles in OWASP Top 10 Proactive Controls.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to not only enhance security awareness, but to build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to grow a security champions program.
In Chapter Four, The Diligent Developers Fortify the Castle from Insecure Design:
As The Diligent Developers continue their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to train your organization on OWASP Top 10 vulnerabilities effectively.