Published on
The OWASP Top 10 is a valuable resource for the AppSec community, as it outlines the most prevalent vulnerabilities that developers must be aware of.
In this article, we will focus on Injection Attacks and advise how to prevent them in your code. We also recommend The Diligent Developer Chronicles as a helpful training resource for your development team.
Read More About OWASP Top 10: OWASP Top 10 Cryptographic Failures Explained
What are Injection Attacks?
Injection attacks are a type of cyberattack that involves injecting malicious code into a vulnerable application. The application can then execute this malicious code, giving the attacker control over the application or the underlying system.
There are four main types of injection attacks to look out for:
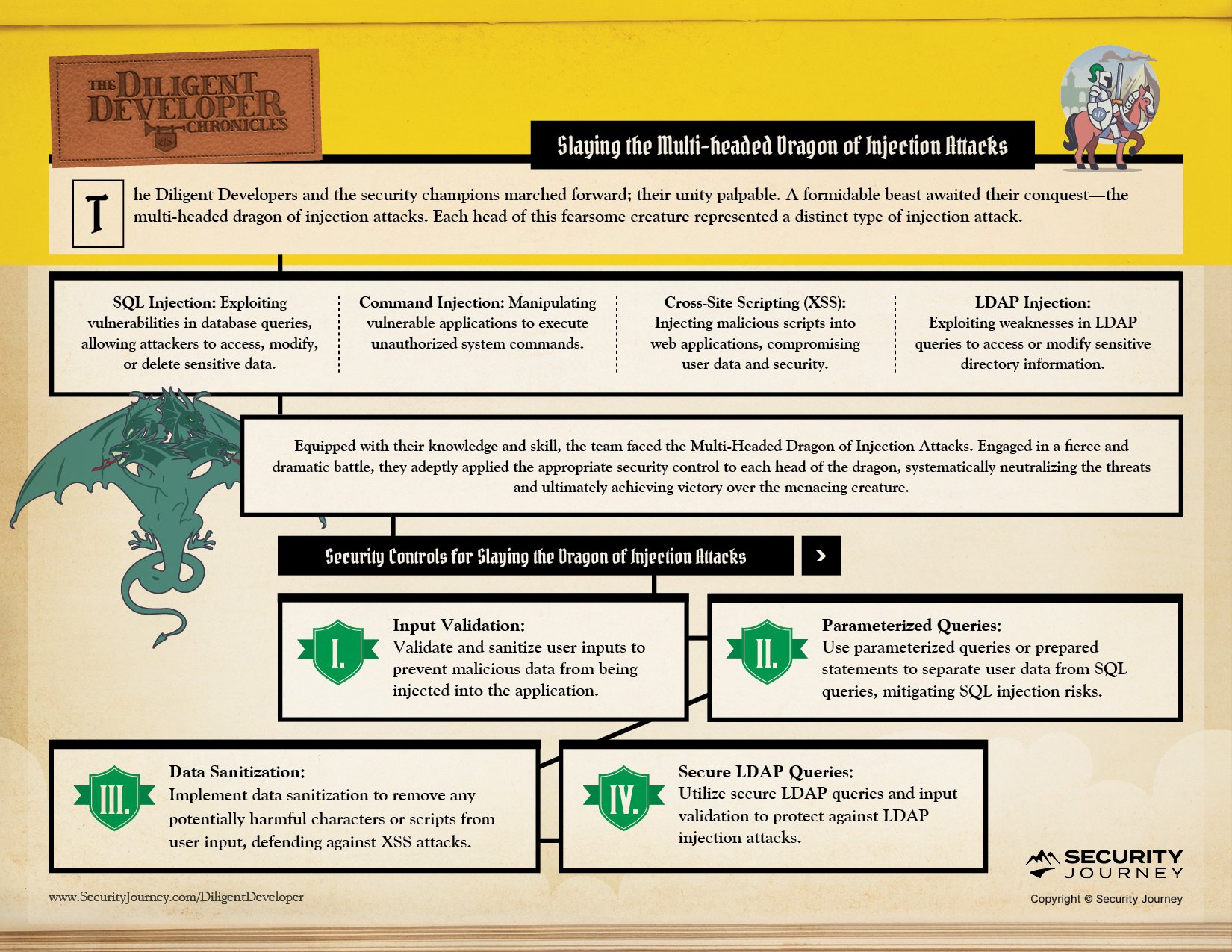
SQL Injection
With an SQL injection, a vulnerability that allowed attackers to exploit weaknesses in database queries, granting unauthorized access, manipulation, or deletion of sensitive data
Command Injection
A command injection is a technique enabling attackers to manipulate vulnerable applications into executing unauthorized system commands
Cross-Site Scripting (XSS)
Cross-Site Scripting injects malicious scripts into web applications
LDAP Injection
An LDAP Injection is an exploitation of weaknesses in LDAP queries, which could grant unauthorized access or facilitate unauthorized modification of sensitive directory information
Read More: OWASP: A03:2021 – Injection
Real-Life Example of an Injection Attack: Colonial Pipeline Attack
The Colonial Pipeline Injection Attack was a ransomware attack that took place on May 7, 2021. The attack targeted the Colonial Pipeline, which is a major pipeline that transports gasoline and jet fuel from the Gulf Coast to the East Coast of the United States.
Colonial Pipeline attack involved the injection of malicious code into the company's systems. The malicious code was used to encrypt the data, but it was not used to steal data or disrupt operations. After a week, the company paid the ransom and the attackers released the decryption key.
Read More on Security Boulevard: The Colonial Pipeline Ransomware Attack: Everything We Know
How Can You Protect Against Injection Attacks?
The key to protecting against injection attacks is to validate user input and use parameterized queries. To learn more, check out this guide on input validation for secure coding.
Here are some ways you can prevent Injection Attacks within your code:
Input Validation
By thoroughly validating and sanitizing user inputs could effectively prevent malicious data from infiltrating the application through injection.
Parameterized Queries
Parameterized queries or prepared statements can separate user data from SQL queries, mitigating the risks posed by SQL injection.
Data Sanitization
To combat XSS attacks, Data Sanitization measures enable the elimination of potentially harmful characters or scripts from user input.
Secure LDAP Queries
For protection against LDAP injection attacks, Secure LDAP Queries and meticulous input validation can protect against any attempts to exploit weaknesses in LDAP queries.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to not only enhance security awareness, but to build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness month initiatives for the entire development team or be used to engage/grow a security champions program -- whatever works best for your organization.
In Chapter Three, The Diligent Developers take on the Multi-Headed Dragon of Injection Attacks:
As The Diligent Developers continue on their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to train your organization on OWASP Top 10 vulnerabilities effectively.