Published on
The OWASP Top 10 is a valuable resource for the AppSec community, as it outlines the most prevalent vulnerabilities that developers need to be aware of.
In this article, we will focus on Broken Access Control and advise how to prevent it in your code. We also recommend The Diligent Developer Chronicles as a useful training resource for your development team.
What is Broken Access Control?
OWASP Top 10 Broken Access Control is a category of security vulnerabilities that allows attackers to gain unauthorized access to resources or perform unauthorized actions such as accessing sensitive data, modifying data, or disrupting the application.
There are many different ways that broken access control can occur. Some common examples include:
- Improper Authorization - This occurs when an attacker can gain access to resources that they should not be able to access. For example, an application that allows users to set their permission levels could be left open for an attacker to designate themselves as an admin and gain control of the application.
- Insecure Direct Object References - This occurs when an application exposes a direct reference to a resource in the URL. For example, an attacker could gain access to an admin account by changing the URL in their browser.
- Mass Assignment - This occurs when an application allows an attacker to inject arbitrary data into an object. For example, an attacker can make themselves an administrator by changing the "isAdmin" property of their user object
Read More: OWASP: A01:2021 – Broken Access Control
Real-Life Example of a Broken Access Control: Snapchat Username Exploit
In 2014, hackers used a Snapchat exploit to compile a list of 4.6 million Snapchat usernames, phone numbers, and locations through access control vulnerabilities. This information was then posted online in a data leak from hackers to gain awareness of the insecurities in the popular social platform.
Read The Forbes Article: 4.6 Million Snapchat Usernames And Phone Numbers Captured By API Exploit
How Can You Protect Against Broken Access Control?
The key to protecting against Broken Access Control is to implement strict usage tracking, validation, and user protocols, and it all starts with a clear understanding of your organization's security requirements.
Here are some ways you can prevent Broken Access Control within your application:
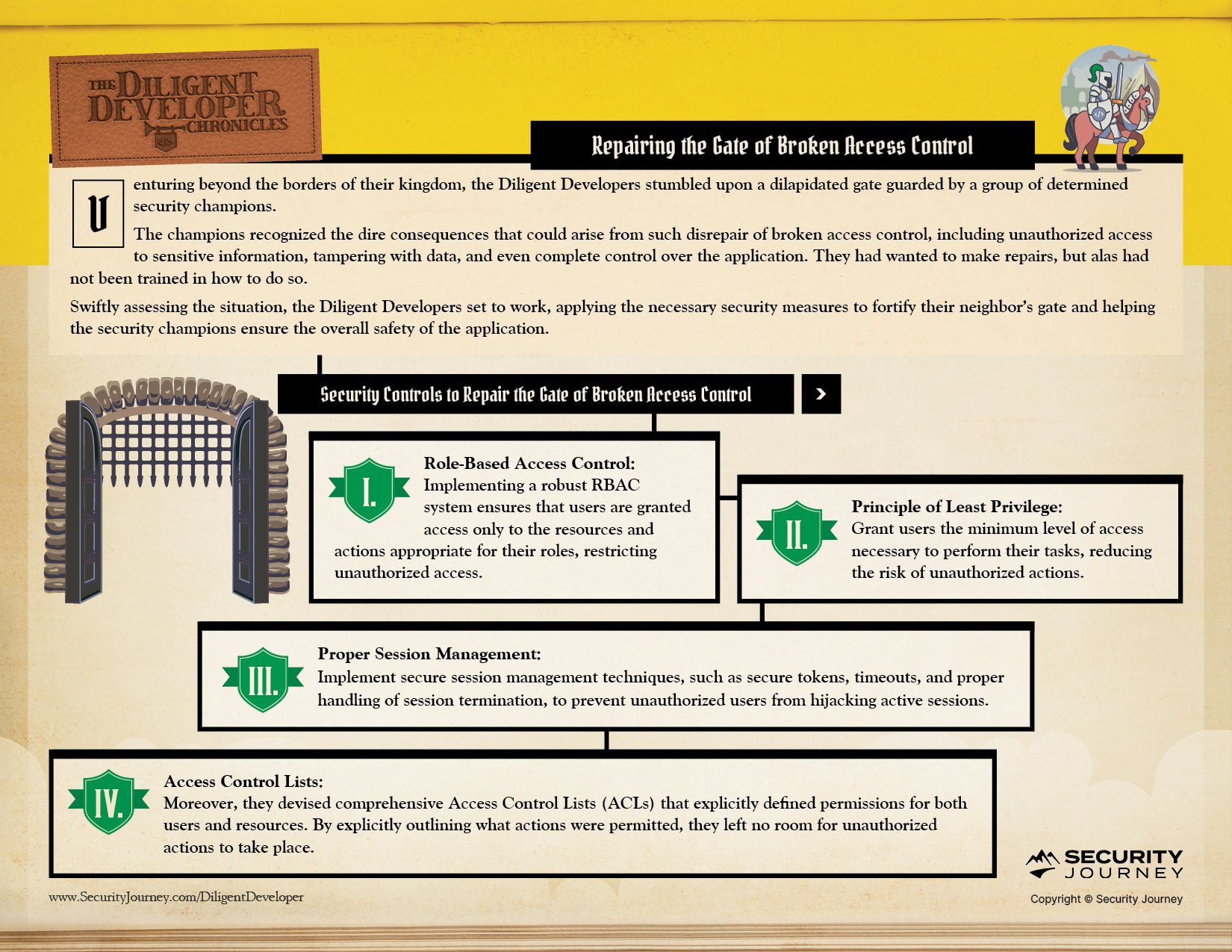
Role-Based Access Control (RBAC) - a robust system that ensures users are granted access only to the specific resources and actions appropriate for their respective roles. By doing so, they effectively restricted any unauthorized access attempts.
Principle of Least Privilege - granting users the bare minimum level of access required to carry out their designated tasks. This approach significantly reduced the risk of unintended actions or unauthorized operations.
Proper Session Management – preventing attempts by unauthorized users to hijack active sessions through measures such as employing secure tokens, implementing timeouts, and ensuring the correct handling of session termination
Access Control Lists (ACLs) - explicitly defined permissions for both users and resources
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks, but also maintain continuous training and conversations about code security across the organization, reinforcing the practices outlined in OWASP Top 10 Proactive Controls.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to not only enhance security awareness, but to build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to grow a security champions program.
In Chapter One, The Diligent Developers take on Repairing the Gate of Broken Access Control:
As The Diligent Developers continue on their journey; stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to effectively train your organization on OWASP Top 10 vulnerabilities.