Published on
Security is more efficient when it comes neatly packaged into the software, i.e., planned, built-in, and shipped with the final product, not thrown in as a last-ditch effort to prevent attacks.
Secure software development, in practice, can be influenced by different frameworks that shape it, the habits that matter most, and secure code training that turns policy into day-to-day skill for developers and teams.
What Is Secure Software Development?
Secure software development is the practice of specifically designing, coding, testing, releasing, and operating software with security embedded at every step of the SDLC. Instead of treating security as a later-stage activity, teams make secure choices in planning and design, encode guardrails in code and pipelines, and verify outcomes continuously. Throughout the entire software development lifecycle, embedding strong protections enhances long-term application safety.
The outcome includes practical risk reduction, faster releases, and evidence that the software will become safer over time. Organizations focused on building secure software consistently outperform peers in resilience, delivery speed, and compliance readiness.
Why Is Secure Software Development Critical in Today’s Threat Landscape?
Attack surfaces expand as organizations add services, integrate third parties, and increase release frequency. Most incidents start with predictable mistakes, not rare zero days. Secure development focuses effort on the patterns that actually cause breaches, lowering vulnerability counts, shortening remediation, and helping teams meet PCI-DSS 4.0, SOC 2, ISO 27001, and NIST SSDF expectations without slowing delivery. Robust security measures across environments reduce the likelihood of successful exploitation from common threats.
What Are the Key Principles of Secure Software Development?
Reliable programs rest on a few durable principles. Teams validate inputs and encode outputs, use secure authentication and session management, apply least privilege with default deny, protect secrets and configuration, and log safely without exposing sensitive data. Pair these with disciplined dependency management, automated checks, and clear ownership so issues are caught early and fixed quickly. Integrating clear software security requirements at this stage helps ensure defenses are built-in, not bolted on.
How Does Secure Software Development Differ From Traditional Development?
Unlike Secure software development, traditional development models isolate security in a late phase, or it is handled by a separate team. Secure development makes security a shared engineering habit.
It is very easy to find that the controls live in pull request templates, coding standards, CI jobs, and deployment policies. Learning is continuous and tied to real findings. The practical outcome is fewer late surprises, calmer releases, and more time for roadmap work. Embedding strong security controls directly in engineering workflows encourages proactive rather than reactive security.
What is a Software Development Lifecycle?
Software development follows what is called a Software Development Lifecycle, or S D L C. It is a process used for developing software. There are several different models which all include the phases of Planning, Defining, Designing, Building, Testing, and Deployment & Maintenance.
The different SDLC models have different time periods for each of the phases and different things they focus on. Some of the more popular SDLC models including Waterfall, Agile, Iterative, Spiral, and V. These models are efficient in satisfying individual requirements of software development organizations, however, none of these models have been built with the consideration of security.
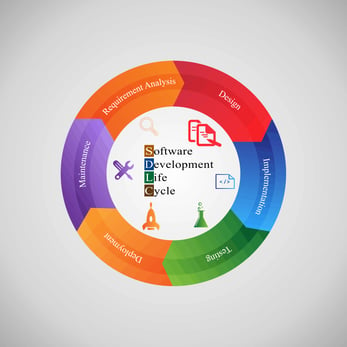
Prior to the inception of the secure SDLC, all security-related activities were performed only as part of the Testing phase. This approach resulted in a high number of undetected vulnerabilities, improper handling of private customer data, an increased number of data breaches caused by cyber-security attacks, and a more expensive Software Development Lifecycle.
In order to avoid the cost and risk associated with the SDLC, organizations started to implement security as a continuous concern in their SDLC model. The Secure SDLC is the process of adding application security into all phases of the SDLC to minimize the risk of vulnerabilities in code. This is the focus of building an effective application security program.
How to Build Security Into Every Stage of the SDLC
There are multiple secure SDLC frameworks that can be followed such as Building Security in Maturity Model (BSIMM), OWASP’s Software Assurance Maturity Model (SAMM), Microsoft Security Development Lifecycle (SDL), ISO/IEC 27034, among others. All of the frameworks have many similarities and in these lessons we are going to focus on best practices from all of them with a little more emphasis on OWASP’s Software Assurance Maturity Model (SAMM).
The SAMM model is technology and SDLC process agnostic and includes Governance, Design, Implementation, Verification, and Operations.
For each of these phases, there are multiple security practices. There is no one security practice that is a silver bullet. Instead, it is the combination of these practices within the SDLC that will reduce the risk of vulnerabilities in software and mitigate the effects when the inevitable vulnerabilities do exist.
Let’s briefly look at the phases of the Secure SDLC:
1. Governance
Governance is focused on building an overall plan, setting the ground rules, standards and regulations, as well as activities related to how an organization should manage its software development process. This phase includes guidelines for employee education and training on cybersecurity, aiming to increase their security awareness around application security. The Governance phase should be conducted as soon as possible. Getting everyone on the same page with expectations and gaining buy-in in an application security program is important and probably the hardest part. In addition, training developers on secure coding has a high return on investment. In Governance, you will develop policies, gain buy-in, and train.
2. Design
The Design phase involves the identification of potential attacks, defining appropriate security requirements to protect the services and data at the core of the application. This phase helps organizations gain a better understanding of the risk and facilitates risk management while also promoting the inclusion of security-related requirements during the software development process. For software that has already been developed post-production analysis can be done to identify and mitigate the risks although it is more complex. In Design, you will add security functions to your applications.
3. Implementation
Implementation promotes the importance of building software in a standardized, repeatable manner and offers guidelines on how to ensure the security and integrity of your applications are not compromised during their deployment. Additionally, it is important to specify how security bugs should be collected, recorded, and analyzed in order to increase security. In Implementation you will create secure build and deployment scripts as well as implement bug tracking software.
4. Verification
Verification is focused on how security testing of the application should be performed. This includes traditional penetration testing and vulnerability assessment audits, automated and manual source code review, and quality assurance tests. Selecting the right Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools are key. In Verification, you will ensure security testing is conducted on applications to find and fix vulnerabilities.
5. Operations
The operations phase specifies how an organization should respond to security incidents, as well as different practices that should be considered to reduce the chances of security incidents proactively. Moreover, it promotes activities required to maintain security throughout the product life cycle. In Operations you will develop an incident response plan, ensure you are logging and backing up applications and data, and put in place additional protections such as monitoring and Web Application Firewalls.
What Frameworks Guide Secure Software Development?
Frameworks give teams a common language, a checklist of minimums, and artifacts for audits. Most programs align to the NIST Secure Software Development Framework (SSDF) for lifecycle structure, the OWASP Top 10 and CWE Top 25 for vulnerability focus, and compliance frameworks such as PCI-DSS 4.0, SOC 2, and ISO 27001. Mapping practices to these standards makes improvement and evidence predictable. Applying these frameworks within the software security development domain reinforces audit readiness and systemic resilience.
What Is the NIST Secure Software Development Framework (SSDF)?
NIST SSDF organizes activities across plan, design, develop, verify, release, and respond. It emphasizes threat modeling, secure design choices, provenance and integrity of components, and verification through code review and testing. Because SSDF is technology neutral, teams implement controls that fit their stack while producing consistent proof for assessors and leadership. Its phased structure maps directly to the modern development lifecycle, helping ensure continuity across roles and responsibilities.
How Do OWASP Standards Support Secure Development?
The OWASP Top 10 highlights widespread web risks like broken access control, injection, and cryptographic failures. The CWE Top 25 catalogs the software weaknesses that lead to real exploits. Using these as anchors helps teams prioritize training, reviews, and tests on the highest-impact issues, then measure progress as those patterns decline. This structured focus helps reduce security risks and align team efforts with critical threat categories.
What Are the Best Practices for Secure Software Development?
High-performing teams that practice secure software development rely on a small set of habits that prevent cybersecurity issues. The checklist below helps to anchor reviews, pipelines, and learning:
- Validate and encode:
Enforce strict input rules and apply context-aware output encoding.
- Harden auth and sessions:
Require MFA where appropriate, use short-lived tokens, set secure cookie flags, and re-authenticate for sensitive actions.
- Limit access by default:
Apply least privilege and default deny for users, services, data, and networks, with periodic access reviews.
- Protect secrets and configuration:
Keep secrets out of source, use a vault, rotate regularly, and separate environments.
- Tidy dependencies: Maintain an SBOM, pin versions, scan continuously, and remove unused packages.
- Log safely
Use structured logs, avoid sensitive data, show safe user messages, and protect log storage. - Automate checks in CI:
Run SAST, DAST, SCA, IaC, and container scans; agree on severity gates that block risky builds. - Review with a checklist: In code review, confirm validation, authorization, secrets handling, error handling, and critical data flows. Following such security practices ensures a higher baseline of safety across all software outputs.
How Do You Integrate Security Into Each Phase of the SDLC?
A practical approach is to add one clear expectation to each phase so security becomes part of the routine, not a separate project.
- Plan: Define data classification, abuse cases, and compliance scope; add security acceptance criteria.
- Design: Run lightweight threat modeling, choose secure frameworks, and document trust boundaries.
- Build: Use secure templates, pre-commit hooks, linters, and secret scanners; follow coding standards.
- Test: Automate SAST, DAST, SCA, IaC, and container checks; add misuse and abuse tests to suites.
- Release: Sign artifacts, verify provenance, and enforce change control.
- Operate: Monitor security metrics, triage findings, practice incident response, and feed lessons back to planning.
By integrating secure checkpoints into each phase, teams can perform secure software development with repeatable and scalable efficiency. This comprehensive software development process must balance speed and security to avoid introducing unnecessary risk.
What Role Does Threat Modeling Play in Secure Development?
Threat modeling helps teams see design risks before code ships. By mapping assets, entry points, trust boundaries, and likely misuse, teams choose controls on purpose rather than reacting later. Keeping models lightweight and tied to high-impact changes makes the practice sustainable in sprint cadence.
Why Are Secure Coding Practices Essential?
Most exploitable security issues begin as coding mistakes. Techniques like parameterized queries, context-aware encoding, explicit authorization checks, safe crypto, and careful error handling eliminate entire classes of bugs. When these habits are built into standards, templates, and reviews, vulnerability counts fall and remediation accelerates.
What Are the Common Challenges in Secure Software Development?
Time pressure, uneven skill levels, and tool fatigue are the most common hurdles in secure software development. Findings can feel disconnected from the work developers do, so lessons do not stick.
Another challenge is fragmented ownership, where no one closes the loop from detection to prevention. The solution is to align training, reviews, scanning, and metrics around the same risks and make progress visible.
How Do You Address Third-Party and Supply Chain Vulnerabilities?
Treat external code and services as part of your system, using the same discipline you apply to first-party code. Maintain an SBOM, scan continuously, remove unused packages, and pin versions. Give preference to well-maintained libraries with a transparent security posture. For APIs, authenticate every call, enforce authorization for each action, validate payloads by schema, throttle, and set strict timeouts. Verify signatures where possible.
What Are the Most Common Security Vulnerabilities Developers Should Know?
Most incidents trace back to a familiar set of weaknesses. Keep these vulnerabilities at the forefront of your mind during design, coding, and review.
- Injection and XSS: Missing validation and unsafe string handling.
- Broken access control: Incomplete authorization checks and overbroad privileges.
- Cryptographic failures: Weak algorithms, bad key management, or plain-text secrets.
- Security misconfiguration: Insecure defaults, open dashboards, permissive CORS, or weak TLS.
- Vulnerable components: Outdated dependencies and unpatched services.
- Identity issues: Session fixation, weak password storage, or missing MFA.
- Logging and monitoring gaps: Noisy logs, sensitive data exposure, or missing alerts.
How Does Developer Training Fit Into Secure Software Development?
Training is how policy becomes skill. Secure code training works best when it is role-based and hands-on, mapped to the team’s languages and frameworks, and delivered in short sessions that match sprint cadence. When the content aligns with real findings and code reviews, developers apply skills immediately, and recurring issues decline.
Why Is Role-Based Security Training More Effective Than Generic Awareness Training?
Generic awareness is easy to skip because it feels irrelevant. Role-based training meets developers in their context, whether frontend, backend, mobile, or DevOps, and goes deep on the frameworks they use daily. Security Journey organizes learning into Foundational, Intermediate, and Advanced paths with monthly updates, so juniors ramp quickly while seniors focus on complex exploits, design tradeoffs, and review leadership.
How Do Hands-On Labs Improve Secure Coding Skills?
Hands-on labs provide full, live applications with complete source visibility, traffic to intercept, and the freedom to fix vulnerabilities in multiple ways. This builds confidence and muscle memory that multiple choice cannot match. Security Journey’s labs mirror production-like systems, so the techniques transfer directly to real services, pull requests, and pipelines.
How Do You Build a Culture of Secure Development?
Culture grows from small, repeatable rituals. Add security prompts to pull request templates, schedule short lessons inside sprint cadence, run fast threat modeling for high-impact designs, and review a simple metrics set every quarter. Celebrate reductions in recurring issues, share brief write-ups when teams fix tricky bugs, and rotate focus areas by product.
What Is a Security Champion and Why Do Organizations Need Them?
A Security Champion is an engineer who mentors peers, promotes good habits, and translates policy into the realities of a service or team. Champions help products move faster with fewer surprises because they understand systems deeply. Security Journey’s Security Champion Passport tracks champion activities and growth, turning individual energy into a durable, measurable culture.
How Do You Measure Developer Security Knowledge and Progress?
Measurement should include learning and outcomes. Use Developer Security Knowledge Assessments to benchmark skills, then track lessons completed, hands-on labs passed, assessment gains, and paths finished. Correlate those signals with vulnerability trends, estimate the mean time to remediate, and note every recurrence of top weakness classes. When a pattern persists, assign targeted labs, tune reviews, and revisit design choices.


