Published on
Do you rely on code scanning tools to ensure your code is secure? Or do you combine code scanning tools with code reviews and secure code training? Recent research shows that code scanning tools alone may not be enough to protect against vulnerabilities.
At Security Journey, our goal is to help your development team write secure code to protect your customers and your organization. Our AppSec Education Platform offers hundreds of lessons to support employees across the SDLC.
In this article, we will review what code scanning tools are, why they may not lead to secure code, and how you can ensure your developers write secure code from the start.
What Are Code Scanning Tools?
Code Scanning Tools, also known as Source Code Analysis Tools, are programs designed to test and analyze code to identify bugs and vulnerabilities before the computer program or application gets pushed live.
There are three types of Code Scanning Tools based on whether the tool is static or dynamic.
- Static Application Security Testing (SAST) - designed to analyze the source code of an application and spot potential issues in the early development stages
- Dynamic Application Security Testing (DAST) - examine a running web application from outside, simulating an actual attack just like a penetration test
- Interactive Application Security Testing (IAST) - analyze the source code of the web application while it is running to identify more vulnerabilities with a lower rate of false positives
Read More: SAST vs. DAST vs. IAST
Top Code Scanning Tools
- GitHub
- Insight AppSec
- GitLab
- HCL AppScan
Why Code Scanning Tools Don’t Work
Code Scanning Tools are a useful and important tool in a development team’s tool kit, but these tools shouldn’t be relied on singularly to secure your code. Let’s review a few reasons why code scanning tools don’t work to fully secure code on their own.
Code Scanning Tools Can’t Catch Everything
Since Code Scanning Tools evaluate code after it’s written, the main goal is to catch mistakes – rather than prevent them. In a recent EMA report, 10% of organizations reported to have prevented a higher percentage of vulnerabilities than organizations not using code scanning tools.
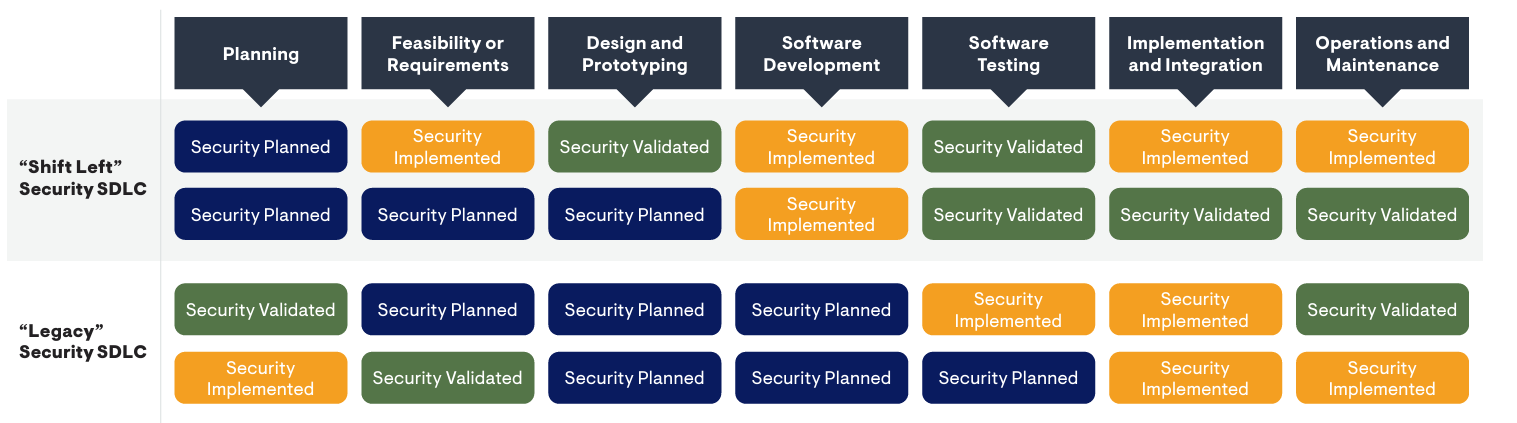
Code Scanning Tools and Third-Party Software and Components
Organizations often use third-party libraries to shorten development timelines, but research shows that additional investment is then required to ensure those third-party libraries are properly vetted, then securely implemented.
While code scanning tools are starting to adopt the capability to evaluate third-party code, it is currently not a default function of common code scanning tools – for example GitHub does offer third-party code scanning capabilities. If you’re not able to scan third party code that you use, you’re leaving your team open to major security risks.
This means that when you are looking to choose a code scanning tool, take the time to find the right fit for your organization.
According to EMA research, organizations that do not use third-party code appear to see great improvements in their code security, but at a slight productivity and application development cost impact.
How To Ensure Developers Write Secure Code
After reviewing the data, EMA believes the best approach to secure software development is a combination of code reviews, code scanning tools, and a stronger emphasis on continuous, third-party training.

Across all industry verticals, software development must shift its focus away from heavily relying on code scanning tools and more on people and processes. 100% of organizations using a combination of code reviews, code-scanning tools, and third-party training saw improvement in their code security.
Secure coding training programs teach developers the necessary skills to solve security threats. The best security education programs teach development teams theory, then ensure that developers build the skills needed to proactively secure applications during the development phase.
Read More: How to Measure the ROI of Application Security Training
It’s better for developers to write secure code initially than to hope that a code scanning tool will catch the vulnerability before it makes it to production – especially when only 10% of organizations utilizing code scanning tools prevent more vulnerabilities than those without.
Should You Invest In Code Scanning Tools?
When working to develop secure code, the more tools in your toolbelt the better. Secure coding training in conjunction with thorough code reviews, and code scanning tools will lead to safer code development.
With a secure coding training platform that integrates with your other tools, your organization decreases their opportunities for vulnerabilities.
With the Security Journey AppSec Education Program, you can leverage the data from your SAST/DAST and bug bounty tools by integrating them with your application security training platform and prioritizing training for the most critical vulnerabilities in your organization.


