Published on
The application security (AppSec) industry has been locked in a perpetual struggle. Threats evolve, yet our defenses often seem stuck in time. Year after year, the OWASP Top 10 list highlights the same vulnerabilities, mirroring the stubbornly consistent patterns in data breach reports.
Despite significant efforts, why are we still grappling with the same problems decades later?
Michael Burch, Director of Application Security, takes a deep dive into how the application security industry can be redefined moving forward.
Current State of Application Security
Our threat landscape hasn't changed over the past 20 years. Yep, you read that right.
The persistence of top threats in the OWASP Top 10 since 2003 paints a concerning picture. It suggests that our application security practices are not keeping pace with the ever-evolving threat landscape. The top threats that we are trying to prevent in our applications haven't changed in the last 10 years – they haven't changed.

The prevalence of data breaches further underscores this point. The number of breach notifications and impacted records has increased (as reported by privacyrights.com) over the past 20 years. Some of this can be more reliance on technologies and better reporting, but the reality is – we've only barely kept the same status and same threats over the last 20 years.
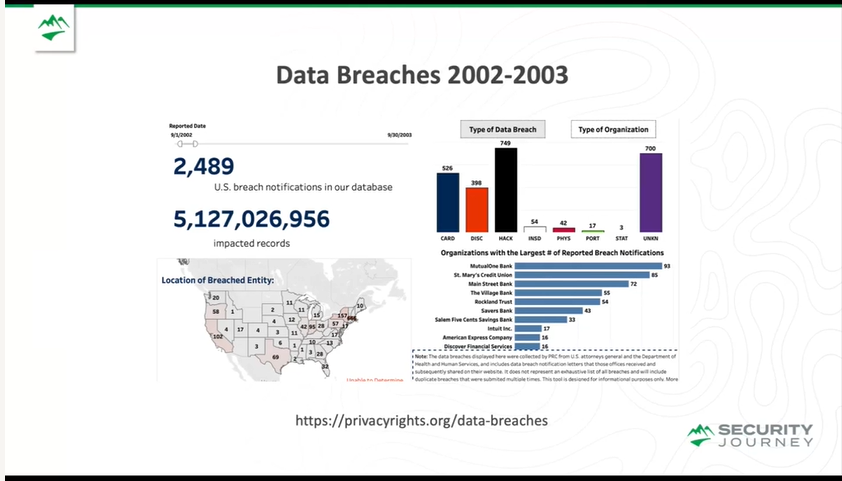
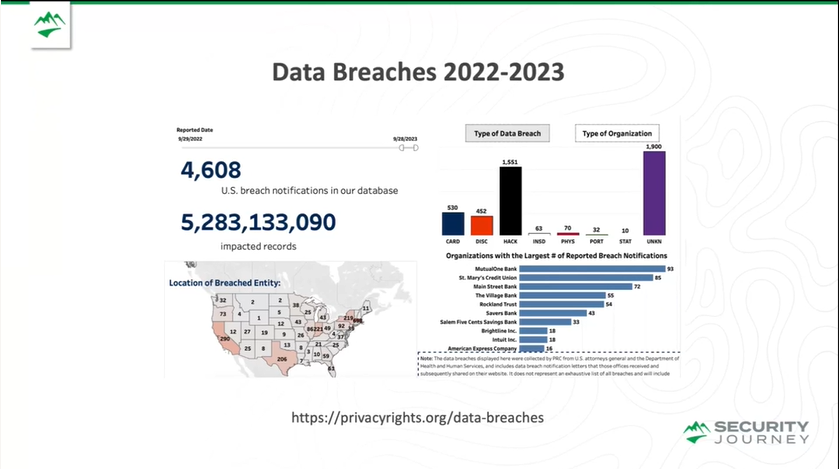
While increased reliance on technology and better reporting practices may account for some of this rise, it's undeniable that the rate of improvement in application security is far from ideal. Essentially, we're stuck in a treadmill effect, running hard just to stay in place.
Read the Article: Top 10 Biggest Security Threats to Your Products
What is the AppSec Dilemma?
At the heart of this stagnation lies the AppSec Dilemma, a complex web of challenges that hinders effective application security.
Let's delve deeper into each facet:
Security Concerns
The OWASP Top 10 has remained remarkably consistent over the years, highlighting vulnerabilities like SQL injection and cross-site scripting (XSS).
These persistent threats expose that attackers are adept at exploiting common coding errors. The ever-increasing number of Common Vulnerabilities and Exposures (CVEs) further underscores this point. New vulnerabilities are constantly emerging, and attackers quickly identify and weaponize them.
Development Pressure
A relentless push for faster development cycles and shorter time-to-market windows characterizes the software development landscape.
This pressure often leads to security being deprioritized in favor of speed. Developers are stretched thin, juggling feature development, bug fixes, and tight deadlines. Security testing and secure coding practices can easily fall by the wayside in this fast-paced environment.
Lack of Security Training
Many developers lack the necessary foundation in secure coding practices. While universities may offer some security-related coursework, it's often not comprehensive or directly applicable to the specific coding languages and frameworks used in the industry.
Even within organizations, security training may be cursory or nonexistent. This knowledge gap makes developers more susceptible to introducing vulnerabilities into their code.
Regulatory Pressure
The regulatory landscape surrounding data security is constantly evolving.
Read The Article: Is Regulation the Consequence of Complacency in Securing Code?
Governments worldwide, especially in the US, are enacting stricter regulations that place greater liability on developers and organizations for data breaches. This increased pressure serves as a wake-up call, highlighting the importance of robust application security practices.
Current Solutions to the AppSec Dilemma
The industry tackles the AppSec Dilemma with various strategies, but their effectiveness is often limited:
- Shift-Left/Shift-Right - While theoretically sound, these buzzwords are more about shifting blame than solving problems. Security should be embedded into every stage of development, not just tacked on at the beginning or end.
- The Tool Trap - Investing heavily in tools without addressing processes or training is a short-sighted approach. Tools are helpful but can't fix the root cause of vulnerabilities.
- "Not My Problem" Mentality - The divide between development and security teams creates a toxic atmosphere, hindering effective collaboration and proactive security measures.
In reality, these approaches function as safety nets rather than root-cause solutions.
It's Time to Change the Game
We cannot find lasting solutions by merely finding bugs faster. The key is to prevent vulnerabilities from being introduced in the first place. Here's where the industry needs a fundamental shift:
- Prioritize Secure Coding Training - Developers need robust education on secure coding best practices. This proactive approach can potentially reduce a massive attack surface at the source.
- Foster Security Champions - Establish a network of security-minded individuals embedded within development teams. This encourages shared responsibility and facilitates security as a natural part of the development cycle.
- Embrace Threat Modeling - Thinking like an attacker must start early. Threat modeling helps teams proactively identify potential weaknesses from the design phase onward.
The Application Security Industry Is at a Crossroads
Continuing with the same approaches, tools, and mindsets guarantees the same problems. By changing how we educate, collaborate, and prioritize security within development, we can finally start turning the tide and make truly secure applications a reality.
You can watch the full webinar from Mike Burch here:


